RADIUS Server: Network Policy configuration
In this example, the Microsoft NPS Server is used. Install the NPS Server role on a Windows system and define a RADIUS client for the switch (steps not included in article).
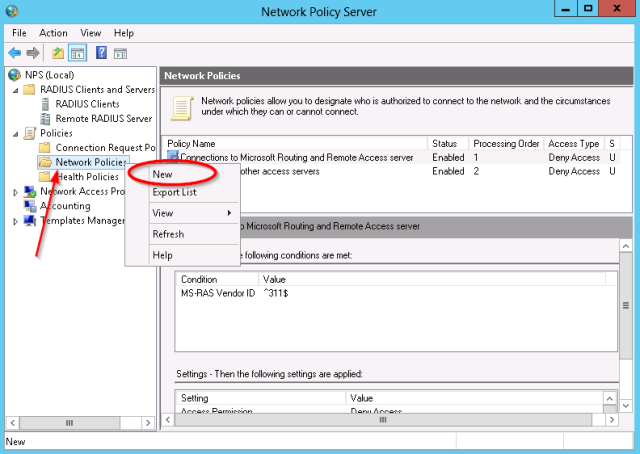
Open the Network Policy Server management console.
- Next, define a new Access Policy:
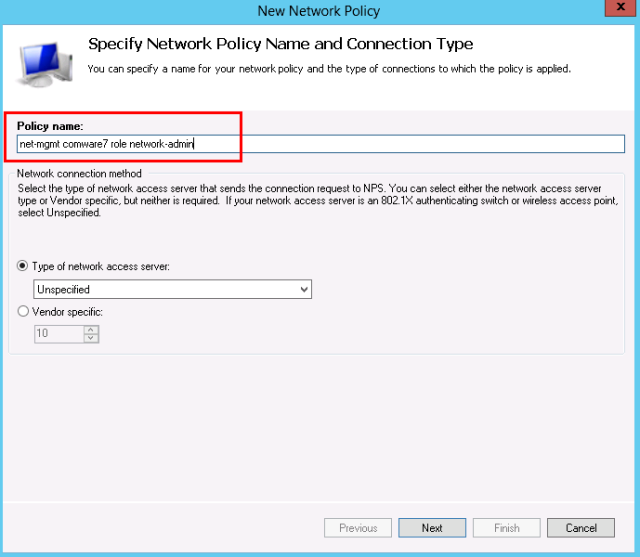
- Enter a descriptive name for the policy.
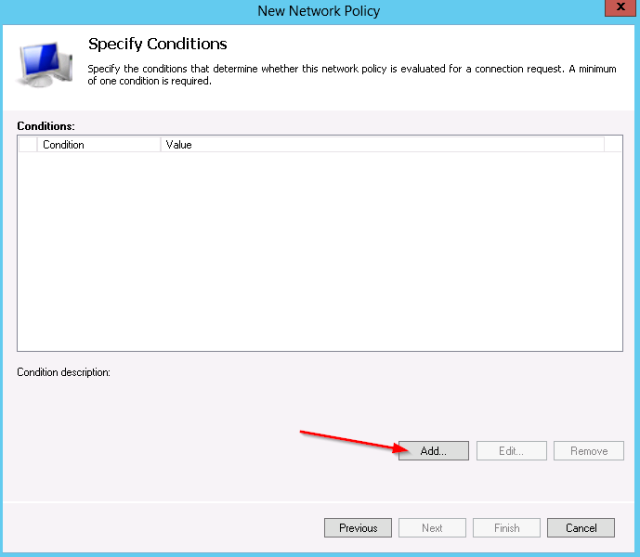
- Next you need to set the matching conditions for this policy. This example will check on:
- Windows group “net-admins”
- Service-type “login”
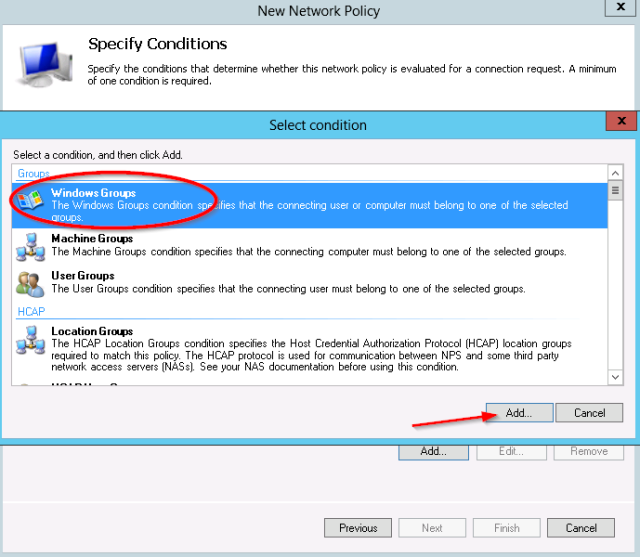
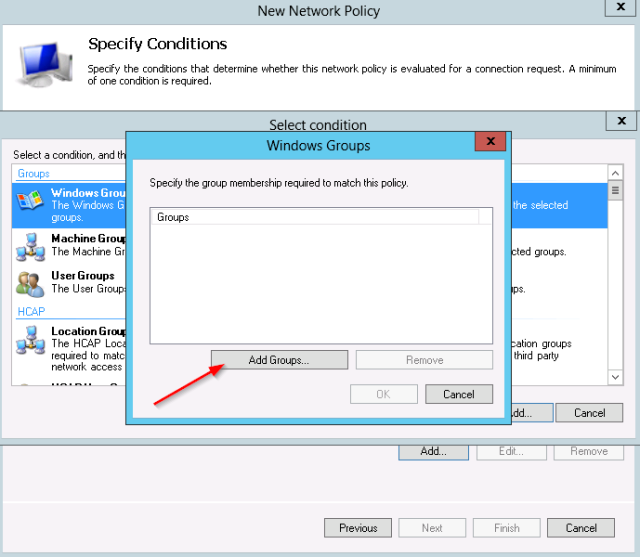
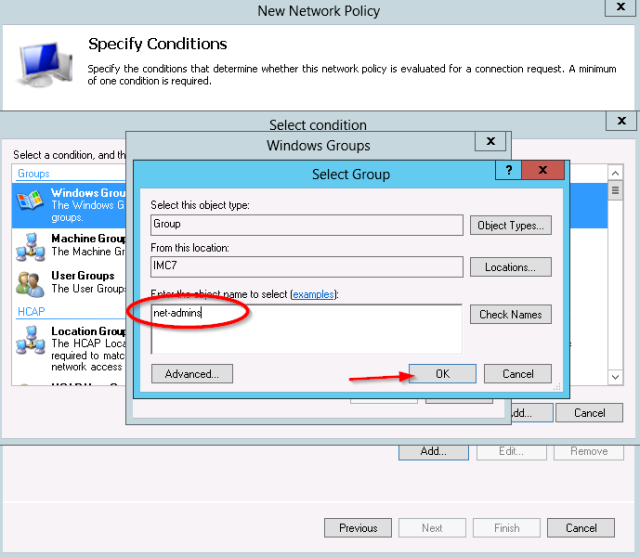
- First add the Windows group condition:
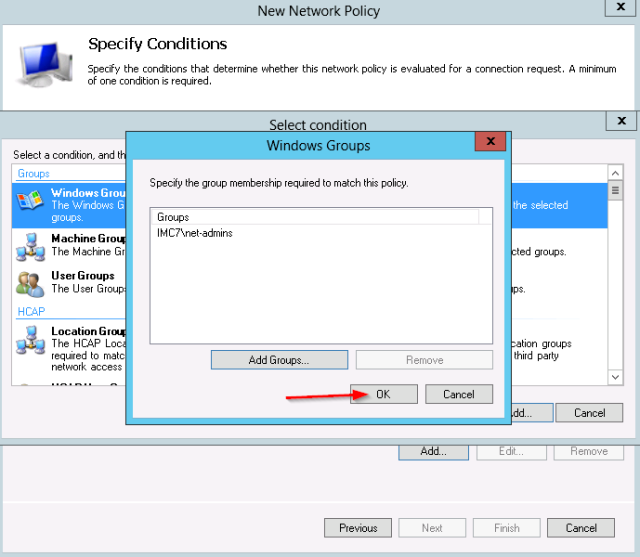
- The test group “net-admins” is selected.
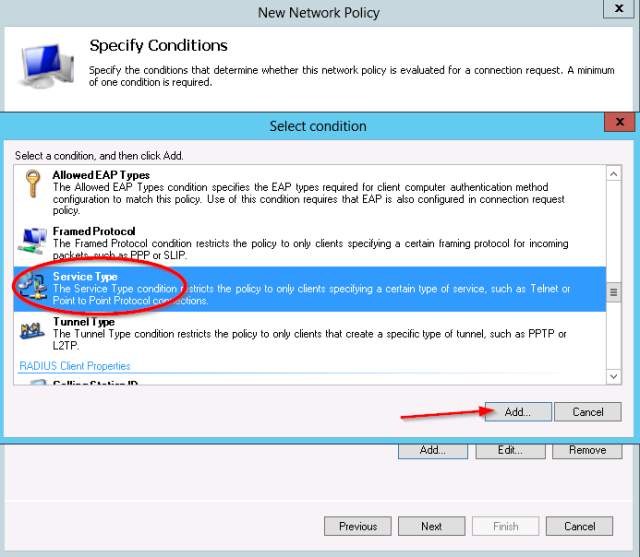
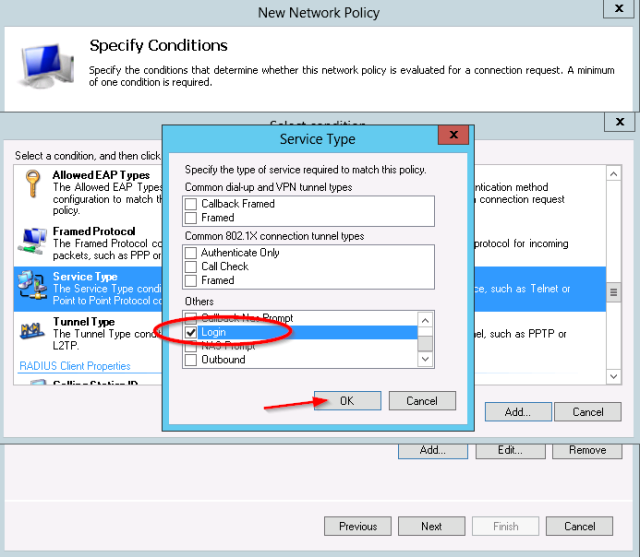
- Next add the service-type condition:
- For the Service-Type, select “Login”
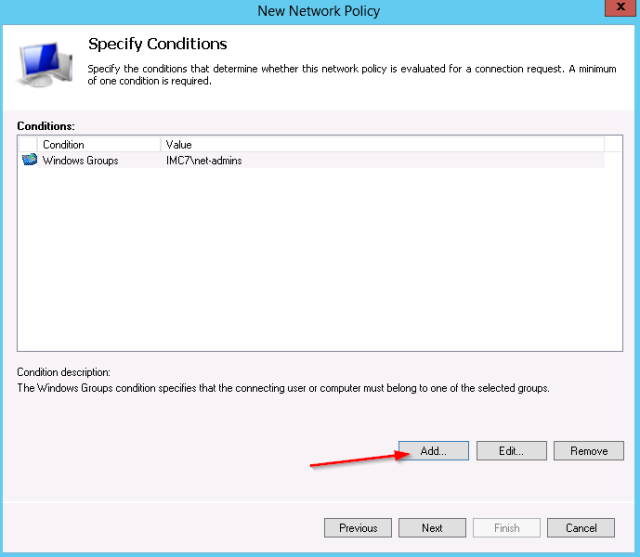
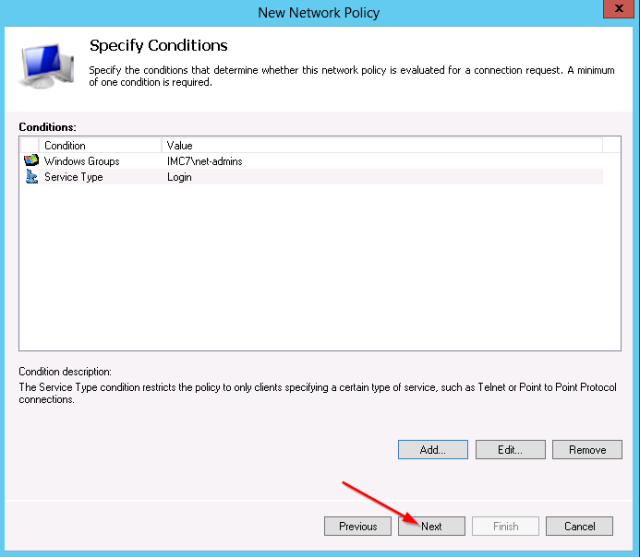
- Verify the 2 conditions:
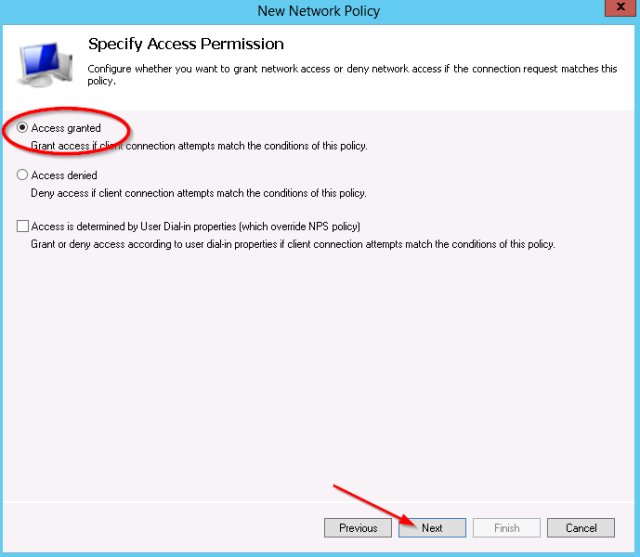
- Leave the access permission to “access granted“
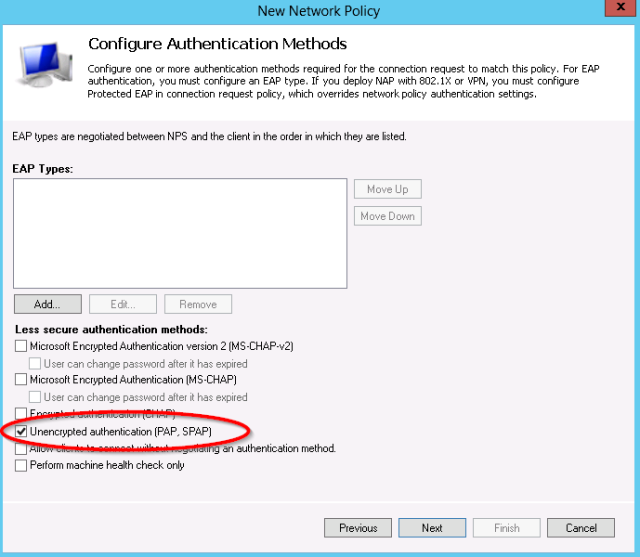
- Admin logins are basic RADIUS login requests, so make sure to enable the clear text PAP/SPAP methods:
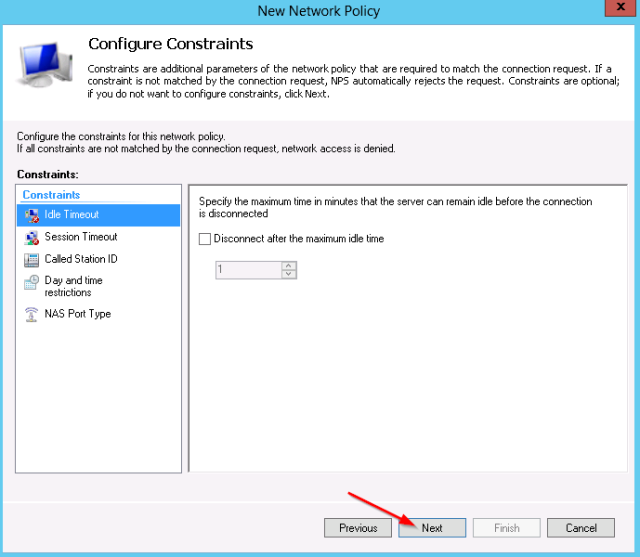
- No other constraints need to be configured:
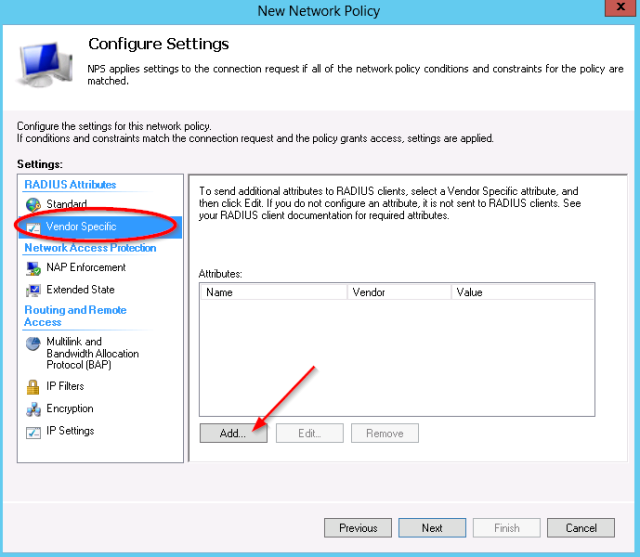
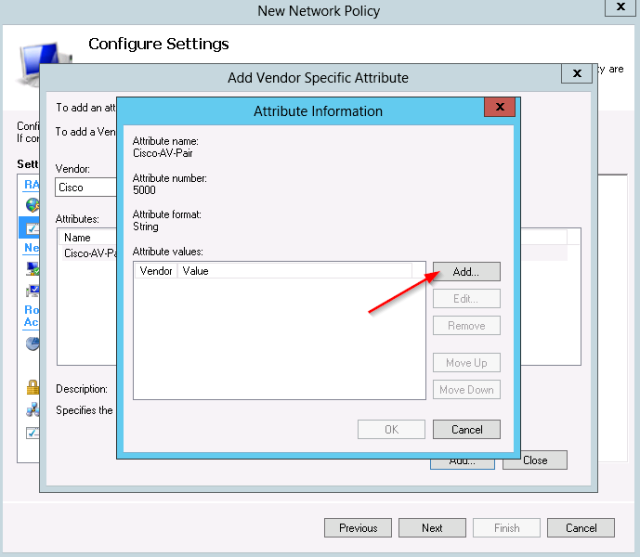
- In the settings which will be applied, select the “Vendor Specific” category.
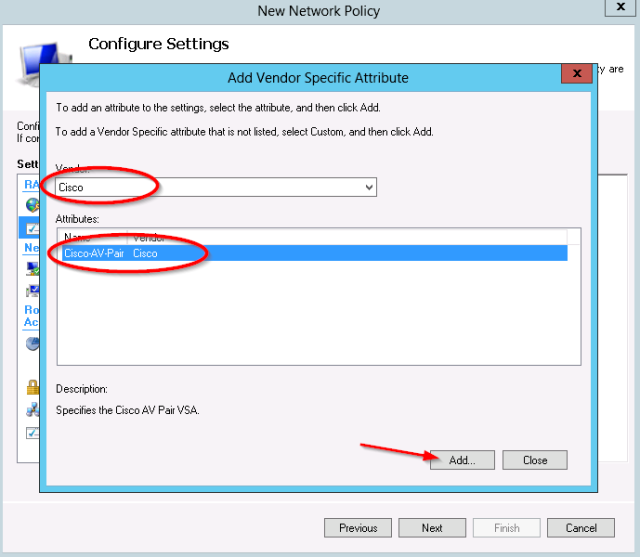
- Select the vendor “Cisco” and the “Cisco-AV-Pair” Attribute:
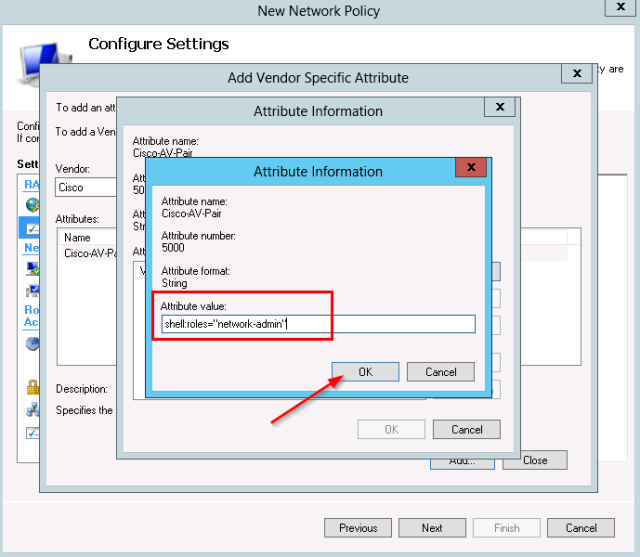
- For the attribute value, set shell:roles=”network-admin”
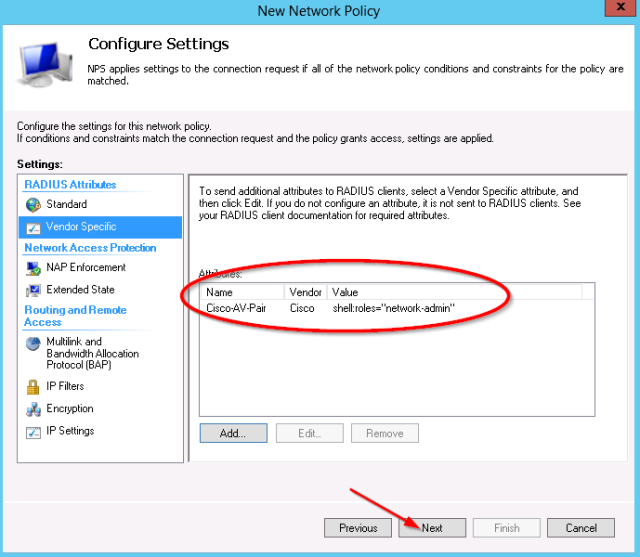
- Review the Vendor Specific settings and finish the wizard.
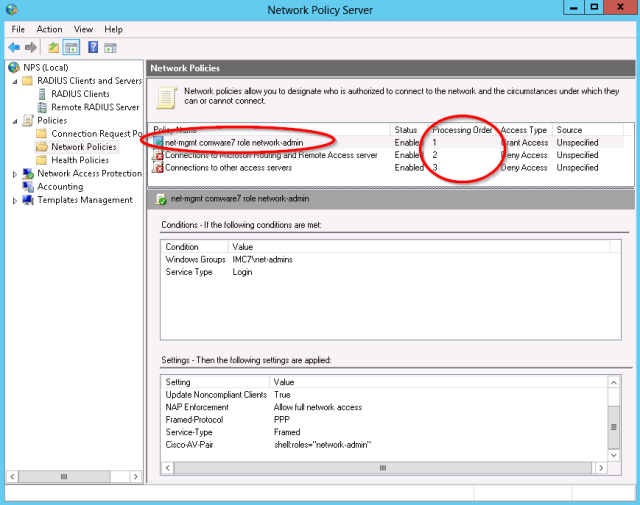
- In the Network policy list, make sure the new policy is placed in front of the block all default policies:
Comware7 Device: RADIUS Server configuration
On the comware7 device, define a radius scheme. The simple password will be automatically saved with a ciphered version. Make sure the key matches the RADIUS Client definitions on the NPS server.
radius scheme nps primary authentication 10.0.1.100 primary accounting 10.0.1.100 key authentication simple hp key accounting simple hp user-name-format without-domain #
Comware7 Device: Domain and line configuration
Next, configure an isp domain (in this example, the default domain system is updated) to use the radius server for administrative logins. Backup authentication is set to none in this example.
domain system authentication login radius-scheme nps none authorization login radius-scheme nps none accounting login radius-scheme nps none #
Configure the line vty range to use the domain authentication scheme
line vty 0 63 authentication-mode scheme
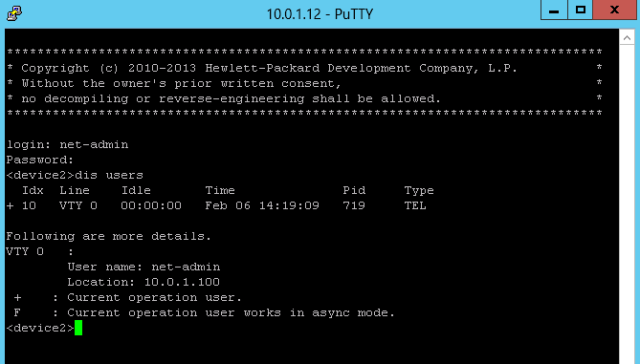
Verify the authentication
Now a telnet client connection is opened, and the test user “net-admin” can login to the device:
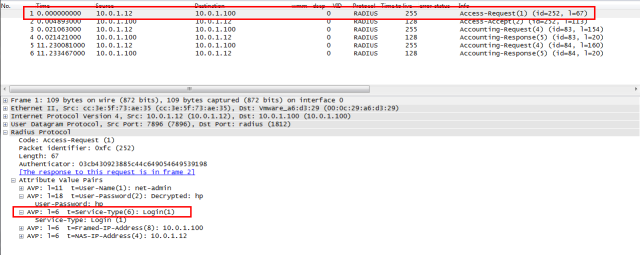
RADIUS network trace
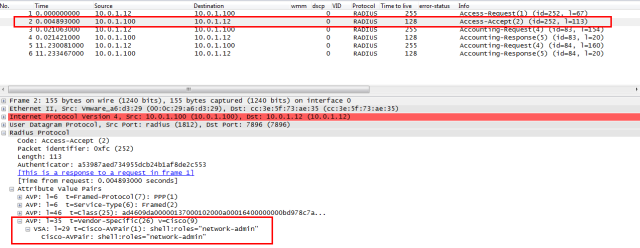
- And the access accept shows the assigned network role
Comware roles
Admin roles can be listed on the comware device with the “display role” command.
This is the filtered example:
<device2>dis role | i Role Role: network-admin Role: network-operator Role: level-0 Role: level-1 Role: level-2 Role: level-3 Role: level-4 Role: level-5 Role: level-6 Role: level-7 Role: level-8 Role: level-9 Role: level-10 Role: level-11 Role: level-12 Role: level-13 Role: level-14 Role: level-15 Role: security-audit
And this would be the detail of the role network-admin:
<device2>dis role name network-admin Role: network-admin Description: Predefined network admin role has access to all commands on the device VLAN policy: permit (default) Interface policy: permit (default) VPN instance policy: permit (default) ------------------------------------------------------------------- Rule Perm Type Scope Entity ------------------------------------------------------------------- sys-1 permit command * sys-2 permit RWX web-menu - sys-3 permit RWX xml-element - sys-4 deny command display security-logfile summary sys-5 deny command system-view ; info-center securi ty-logfile directory * sys-6 deny command security-logfile save R:Read W:Write X:Execute <device2>
Refer to http://abouthpnetworking.com/2014/03/16/comware7-radius-based-rbac-user-role-assignment/


0 comments
Post a Comment